A security flaw found in Touch ID and Face ID biometric authentication features may have had some unsettling real-world implications.
The bug, originally discovered back in February 2020, could have provided threat actors with unauthorized access sensitive data as long as users opted for these biometric controls to sign into their iCloud accounts in Safari. Thankfully, Apple has since rolled out a patch for this imperfection.
What was the exploitation mechanism like? When attempting to sign in to a website with Apple ID in the Safari browser, users can choose to leverage Touch ID and thereby circumvent two-factor authentication (2FA). Such a method differs from the commonplace way of accessing Apple domains through the use of the ID and password combo, where the verification process is managed by an iframe embedded on that web resource and tied to Apple’s login validation server.
If Touch ID is the user’s choice, the iframe routine is modified to handle biometric authentication and the retrieval of access tokens along the way. To this end, the daemon interacts with an Application Programming Interface (API) residing on the gsa.apple.com domain, which receives the request data and sends the valid token. The vulnerability was in the API tasked with providing a domain abuse functionality. It could pave the way for a cross-site scripting (XSS) condition exploitable on any subdomain. The authentication-related daemon that enabled this quandary is called “akd”.
Thijs Alkemade, a security analyst who identified the loophole, said that although the vulnerable API received the “client_id” and “redirect_uri” values from “akd” daemon, it did not verify whether these parameters were an exact match. The checks were isolated to a whitelist applied on the domains, which means that any domain that ends with apple.com, icloud.com, and icloud.com.cn was allowed.
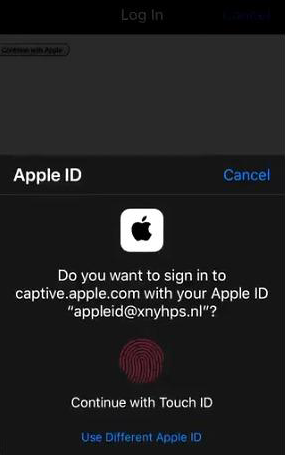
According to Alkemade, one more viable attack vector in this regard comes down to injecting JavaScript on the site when a connection is being established with a Wi-Fi access point for the first time. A rogue wireless network could generate a response in the form of a page containing JavaScript code that executes OAuth as iCloud.
As a result, the user gets a Touch ID dialog whose purpose isn’t clear at all. In case the user proceeds with biometric sign-in via this dialog, the session token is automatically submitted to the harmful site. This allows the adversary to initiate a session for the user’s account on iCloud.
If a bogus hotspot is created in a hotel, at an airport, or in another place where people normally expect to interact with a captive portal before establishing a wireless connection, attackers could compromise a lot of iCloud accounts in one hit. This, in turn, poses risk to the victims’ backups, photos, geolocation, and many more sensitive details.
